Wikipedia: HTTP Strict Transport Security (HSTS) is a web security policy mechanism which helps to protect websites against protocol downgrade attacks and cookie hijacking. It allows web servers to declare that web browsers (or other complying user agents) should only interact with it using secure HTTPS connections, and never via the insecure HTTP protocol.
Add this line of code into your server block:
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains; preload" always;This header tells nginx to add STS header to the response and compatible clients will react accordingly the next time they visit this website. Even though you specify http: in the address bar, the browser will make a request using https automatically. However, that is not all. What if the hijack happens when the client first visits the website before you even have the chance to return an STS header?
Nginx Blog: When a user enters a web domain manually (providing the domain name without the http:// or https:// prefix) or follows a plain http:// link, the first request to the website is sent unencrypted, using plain HTTP. Most secured websites immediately send back a redirect to upgrade the user to an HTTPS connection, but a well-placed attacker can mount a man-in-the-middle (MITM) attack to intercept the initial HTTP request and can control the user’s session from then on.
To protect against that scenario, the clients (browsers) need to know that they have to use https only if they are sending a request to that website. Even before they visit the website for the first time. This is solved by having a preload list in the browser itself.
Major browsers such as Chrome, Firefox, IE11, Edge, Safari and Opera have a preload list included. The list is maintained by Chrome and you can submit your application here. After you met all the criterias and successfully enrolled, you will see the status is pending submission to the preload list.
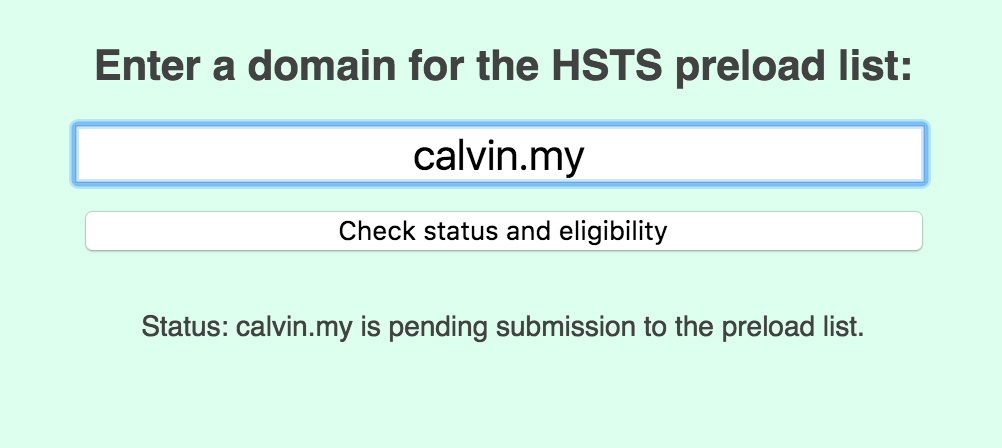
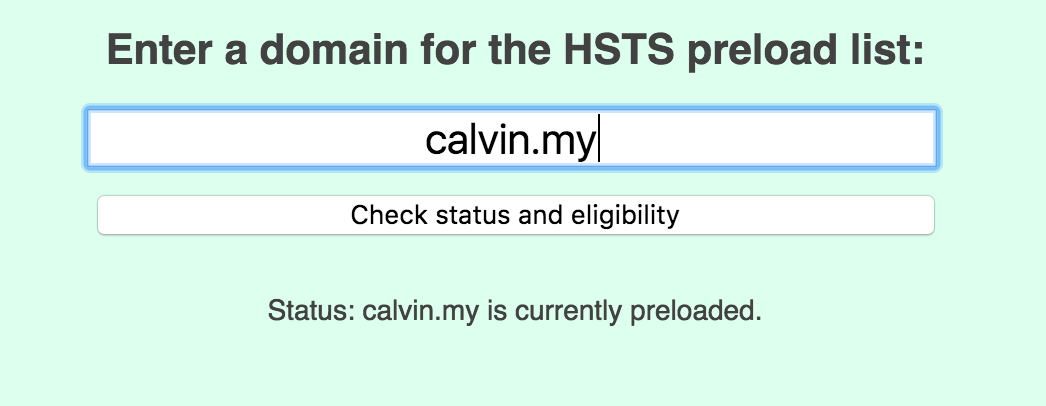
It will take a while (maybe months) before your website is included in the preload list of these browsers. When the browsers adopted the list which includes your domain name, you will see the status is preloaded.
Note: For chrome, you can query the HSTS set by visiting chrome://net-internals/#hsts